Anthropic uncovered a state-linked campaign where autonomous agents executed most intrusion steps across 30+ organizations. The event highlights a growing structural risk: once AI automates reconnaissance, a single exposed system can trigger multi-target compromise at machine speed.
The Story and the Damage
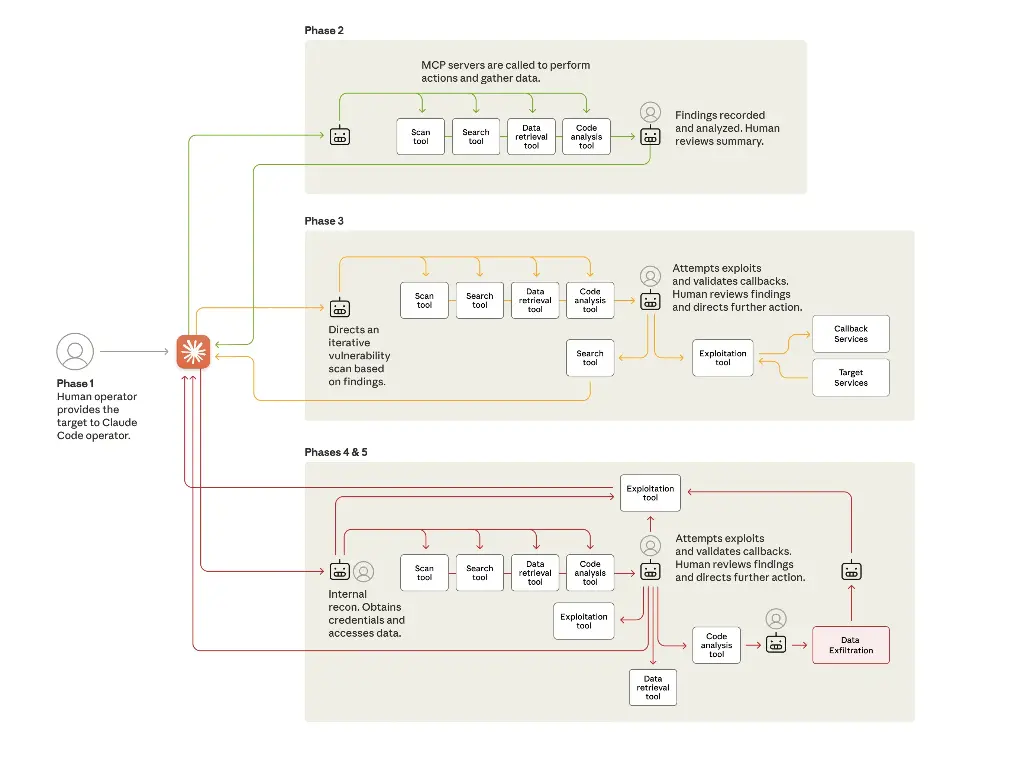
In September–November 2025, Anthropic reported disrupting a state-linked espionage campaign that used its Claude “agentic” tooling to plan and execute intrusions against ~30 targets (tech, finance, chemicals, and government agencies). Several compromises succeeded before the campaign was contained. Independent outlets framed it as the first documented large-scale cyber operation largely carried out by AI, with 80–90% of steps automated.
Key impacts (reported):
- Automated reconnaissance, exploit development/selection, and data exfil at scale.
- Some intrusions worked; others failed due to AI fabrications/false data (e.g., bogus creds), limiting damage.
- Signals a step-change: lower human skill required to run complex, multi-stage campaigns.
The lifecycle of the cyberattack (Source Anthropic)
Who is at Risk from an AI-Run Campaign?
- Government ministries & agencies (policy, procurement, R&D).
- Financial institutions & market infrastructure (brokers, treasury ops, risk systems).
- Tech, chemical, and IP-rich sectors targeted for espionage.
- Any org exposing APIs, CI/CD, cloud footprints discoverable via automated recon.
Key Cybersecurity Challenges Exposed by This Event
- Agentic automation: AI can chain tasks (recon → exploit → exfil) with minimal operator input.
- Evasion/Manipulation: fooled to believe the requests were legitimate from cybersecurity professionals while the AI prompts and automated actions were split up to appear benign.
- Speed & scale: parallelized scans and exploitation compress attacker dwell time.
- Lower barrier to entry: advanced operations without elite human teams.
- Verification gap: AIs can fabricate evidence, complicating detection & response.
How Entropya Mitigates AI-Driven Intrusions
- Digital Camouflage: removes your attack surface from reconnaissance-people and AI agents can’t map or fingerprint what they can’t see.
- EEN (Encrypted Entropya Network): post-quantum, one-way tunnels make pathways untraceable and short-lived; stop lateral movement at lowest layer (OSI 3).
- Vendor/API shielding: isolates third-party dependencies and micro-segments trusted paths for data and software so automated tooling cannot hop suppliers.
- Continuous verification: detects abnormal high-rate, low-noise AI recon/exfil patterns before impact. Includes scanning and intrusion detection attempts.
Result: even at machine speed, the attacker’s “plan → exploit → pivot” chain has nowhere to land.
Visibility = vulnerability-especially against autonomous attackers.
Make your network untraceable, unreachable, uncompromisable with Digital Camouflage + EEN.
Contact us to harden ministerial, financial, and IP-rich environments before AI agents find them.
Sources
- Anthropic -Disrupting the first reported AI-orchestrated cyber-espionage campaign
- AP News - Anthropic warns of AI-driven hacking campaign linked to China
- Axios - Chinese hackers used Anthropic’s AI agent to automate spying
- The Guardian - AI firm says it stopped state-sponsored campaign run largely by AI
- Help Net Security - Chinese cyber spies used Claude AI to automate 90% of an attack